- Accelerating Success: How Cisco and Partners Drive Cybersecurity Growth
- IoT security: Challenges and best practices for a hyperconnected world
- The LG C4 OLED is over 50% off right now - and trust me, it's worth every penny
- You can win $250K from OpenAI if you help solve archaeological mysteries with AI
- Red Hat releases tool to manage edge devices at scale... and to drive cars
How CISOs can Mitigate Cryptomining Malware

Risk Management
Learn more about cloud-based cryptomining, its repercussions, and how CISOs can create an effective risk mitigation strategy for this threat.
Read time: ( words)
As cryptocurrencies continue to grow in popularity, organizations are increasingly at risk for cryptomining attacks. In fact, Apache Log4j (Log4Shell)—the holiday gift no one asked for—was observed to be mostly used for cryptomining and ransomware by cybercriminals. Trend Micro Research investigated the most prominent groups in the cryptocurrency-mining landscape to determine the impacts on organizations and establish best practices for effective risk mitigation.
What is cloud-based cryptomining?
Malicious cloud-based cryptomining or cryptocurrency-mining malware is when cybercriminals enter cloud deployments by exploiting unpatched vulnerabilities, weak credentials, or misconfigurations to utilize an organization’s compute power to generate cryptocurrency.
Business repercussions of cryptomining
1. Resource consumption and cost
Perhaps the most obvious impact—cybercriminals mooching off compute power leads to significant spikes in cloud computing costs. This is especially worrisome if the cloud environment is set to auto-scale; legitimate projects can be scaled up and cost more, making cryptomining difficult to detect until the bill comes in. For example, when Trend Micro Research deployed the monero miner, XMRig, on one of its systems, they saw a drastic 600% increase in CPU costs from US$20 to US$130 per month.
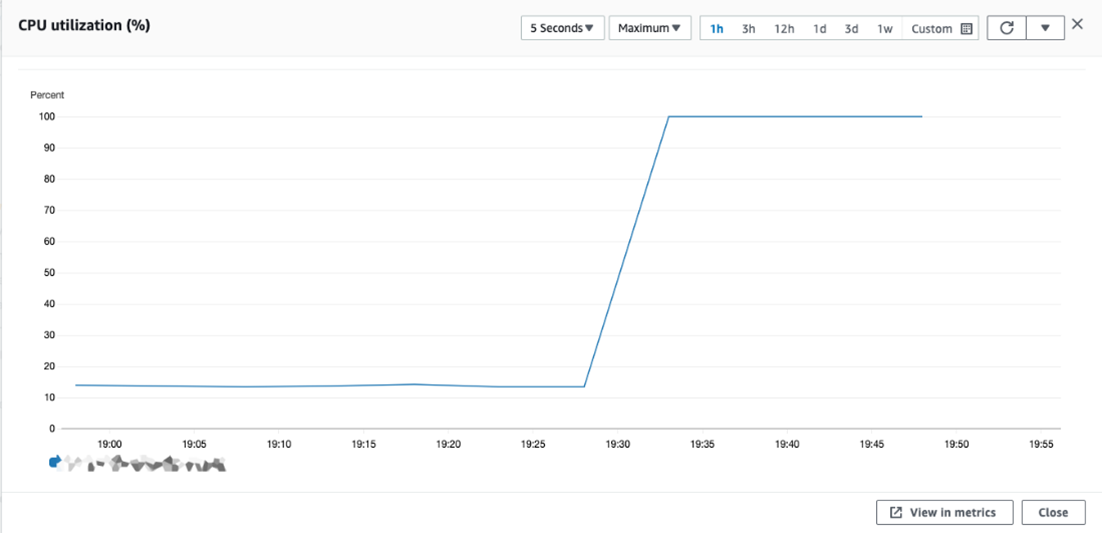
2. Business downtime
Even if you do not see the direct impact with fixed pricing of your cloud infrastructure, the uptick in CPU consumption can also cause systems to lag, directly impacting business operations. Not only do disruptions impact internal workflows, but interruptions to online services can also lead to customer dissatisfaction, reputation loss, and revenue decline.
3. Part of a larger attack
While organizations are often concerned with fending off data exfiltration or ransomware attacks, cryptomining should be regarded with the same seriousness. Trend Micro Research compared a successful cryptocurrency-mining attack to “a canary in a coal mine”—meaning it’s an indicator of poor security hygiene that can expose a business to a gauntlet of attacks. Essentially, cryptomining groups use the same tools and techniques to gain access to their targets’ systems that can used by other groups such as access-as-a-service or ransomware-as-a-service actors.
Cryptomining mitigation strategies
Since cryptomining groups use the same attack tactics as other cybercriminals, defending against this threat will also bolster your security posture across your enterprise. This means you don’t need to scour the market for yet another point product designed to specifically defend against cryptomining. By leveraging a unified cybersecurity platform, you can address cryptocurrency-mining attacks and other critical threats without further complicating detection and response for security teams.
Look for a platform with the following capabilities to help you and your security teams better understand, communicate, and mitigate threats across the enterprise:
- Continuous attack surface monitoring to effectively address risk, including suspicious user behavior. Leveraging the Zero Trust approach ensures only validated users, devices, and applications are granted access and if any suspicious activity is identified, access should be immediately terminated.
- Virtual patching to minimize the chance of vulnerability exploitation in outdated software versions before a vendor patch is released or to help with your current patch management process.
- Extended detection and response (XDR) to collect and correlate deep security data across endpoints, email, network, and cloud for enhanced visibility and faster detection and response.
- Intrusion detection and prevention systems (IDS/IPS) that can limit and filter both ingress and egress network protection for known exploits.
- Customizable rules to monitor resource utilization, track open ports, and check the usage of and changes made to DNS routing.
- Leverages industry standards and frameworks such as MITRE ATT&CK to help defenders identify the most common tactics and techniques (TTPs) observed amongst cloud-based cryptomining groups.
For more security insights into the cryptomining landscape, check out our extensive research report and one-page primer. To learn more about the benefits of leveraging a unified cybersecurity platform, explore these resources:
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

